42 antivirus policy in cyber security
Create a cyber protection policy for your small business ... What's more, as most cyberattacks tend to exploit basic vulnerabilities in systems, they are easy to prevent with antivirus software, patch updating and staff awareness training. A cyber protection policy means your staff will be better informed and able to take appropriate action to prevent attacks Endpoint security AV-Comparatives tests Anti-Virus Software protection ... Consumer Anti-Virus Vendors Avast, AVG, Avira, Bitdefender, ESET, G Data, K7, Kaspersky, Malwarebytes, McAfee, Microsoft, NortonLifeLock, Panda, Total Defense, TotalAV, Trend Micro and VIPRE. The Hermetic Wiper malware threats have been tested using the Real-World Protection Test framework, developed by AV-Comparatives.
Malware & Ransomware | Cybersecurity Malware is short for "malicious software." It is a program or file designed to be disruptive, invasive and harmful to your computer. Types of malware include viruses, spyware, adware and worms. Malware frequently strikes the Ohio State campuses, causing varying degrees of trouble. It is most frequently transmitted through e-mail attachments ...
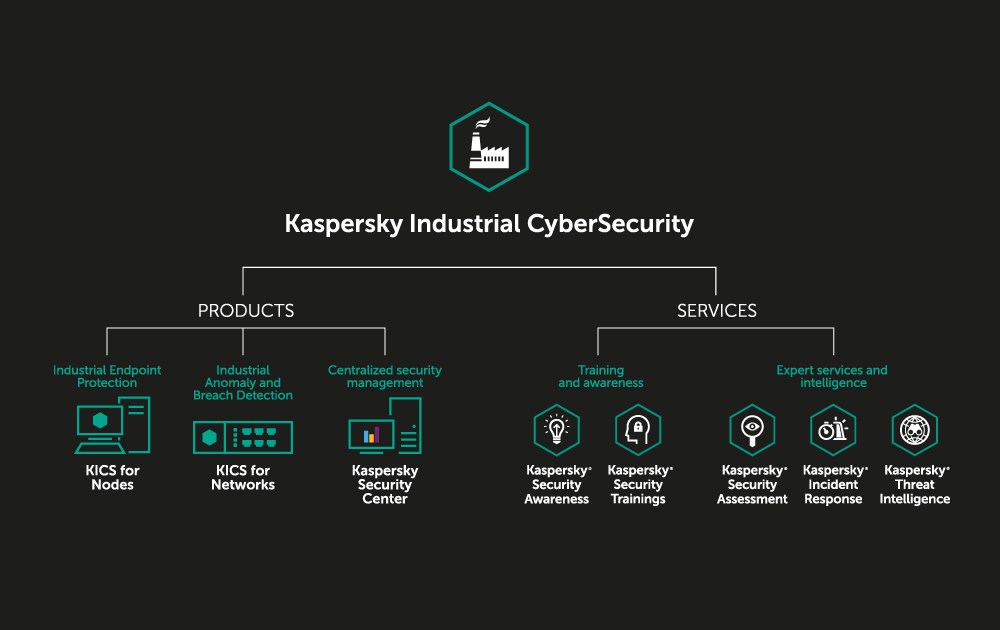
Antivirus policy in cyber security
Information Security Policy Examples | EDUCAUSE IT Policies at University of Iowa. University of California at Los Angeles (UCLA) Electronic Information Security Policy. University of Notre Dame Information Security Policy. University of Iowa Information Security Framework. Carnegie Mellon Information Security Policy. Stanford University Computer and Network Usage Policy. 84% of Indian Organizations Falling Short on Data ... According to Veeam's Data Protection Trends Report, 84% of Indian organizations suffered ransomware attacks, making cyber-attacks one of the single biggest causes of downtime for the second ... Cyber security policy template | TalentLyft We recommend employees to follow these best practices: Keep all electronic devices' password secured and protected Logging into company's accounts should be done only through safe networks Install security updates on a regular basis Upgrade antivirus software on a regular basis Don't ever leave your ...
Antivirus policy in cyber security. Cybersecurity | Homeland Security Cybersecurity. President Biden has made cybersecurity, a critical element of the Department of Homeland Security's (DHS) mission, a top priority for the Biden-Harris Administration at all levels of government. To advance the President's commitment, and to reflect that enhancing the nation's cybersecurity resilience is a top priority for ... Cybersecurity for Small Business | Federal Communications ... 10 Cyber Security Tips for Small Business Broadband and information technology are powerful factors in small businesses reaching new markets and increasing productivity and efficiency. However, businesses need a cybersecurity strategy to protect their own business, their customers, and their data from growing cybersecurity threats. What Is Cybersecurity | Types and Threats Defined ... The technology you'll use to prevent and combat cybersecurity attacks, like DNS filtering, malware protection, antivirus software, firewalls and email security solutions. The technology your data lives on that needs your protection, like computers, smart devices, routers, networks and the cloud. Cybersecurity - Cisa In light of the risk and potential consequences of cyber events, strengthening the security and resilience of cyberspace has become an important homeland security mission. CISA Cybersecurity Services Explore the cybersecurity services CISA offers and much more with the CISA Services Catalog .
resources.workable.com › cyber-security-policyCompany cyber security policy template - Workable Company cyber security policy template This Company cyber security policy template is ready to be tailored to your company’s needs and should be considered a starting point for setting up your employment policies. Policy brief & purpose Our company cyber security policy outlines our guidelines and provisions for preserving the security of our ... Data privacy and cyber security: the importance of a ... Technical policies may include a variety of commitments to technical controls to ensure the protection of data, including encryption, passwords, authentication protocols, disaster recover, intrusion detection, physical security, patching and the like. For companies with a public-facing website, website privacy policies are a must. AntiVirus - Cybersecurity The first step a user must make is to decide which antivirus program will be best for them. There are many free and paid... When installing the antivirus program, it is best to set up scheduled updates. The antivirus program will usually prompt... Ensure scans are performed at regular intervals. We ... antivirus.comodo.comDownload Free Antivirus Software | Get Complete PC Virus ... We are offering the best value on the market because we strongly believe in creating a cyber-safe environment for everyone. We are a company that develops the most advanced cyber-security solutions for enterprise businesses, and we use that same technology to protect homes across the world with Comodo Antivirus.
Cybersecurity for Nonprofits | National Council of Nonprofits The types of losses/expenses that cyber insurance can cover range from the cost of notifying all the folks whose information may have been comprised; to the cost of content repair, such as repair to a hacked website; to the cost of hiring a PR whiz to help your nonprofit recover its reputation after a severe security breach. There are even some ... Cyber Security Audit - Isaca KEY ELEMENTS OF CYBER SECURITY AUDITING: CONTROLS AND THREATS Part of auditing is ensuring that organizations have implemented controls. This means that preventative tools such as firewalls and antivirus software have been put in place. It also means that awareness efforts have been made, and that user education about Information Technology Security Plan Anti-‐virus Policy (10.6) SSU network are hardened against attack and protected by antivirus software at all times. 3.0. Applicability. This policy applies to all employees, ...2 pages f-secure.comCyber security solutions for your home and business | F-Secure Nobody knows cyber security like F‑Secure. For three decades, F‑Secure has driven innovations in cyber security, defending tens of thousands of companies and millions of people. With unsurpassed experience in endpoint protection as well as detection and response, F‑Secure shields enterprises and consumers against everything from advanced ...
9 policies and procedures you need to know about if you're ... 9 policies and procedures you need to know about if you're starting a new security program Any mature security program requires each of these infosec policies, documents and procedures.
Create a cyber security policy | business.gov.au A cyber security policy outlines: technology and information assets that you need to protect; threats to those assets; rules and controls for protecting them and your business; It's important to create a cyber security policy for your business - particularly if you have employees. It helps your employees to understand their role in ...
What is Cybersecurity? | IBM Cybersecurity is the practice of protecting critical systems and sensitive information from digital attacks. Also known as information technology (IT) security, cybersecurity measures are designed to combat threats against networked systems and applications, whether those threats originate from inside or outside of an organization. In 2020, the average cost of a data breach was USD 3.86 ...
PDF Information Management and Cyber Security Policy Cyber Security Policy March 2010 . 2 ... Information security refers to the protection of information from accidental or unauthorized access, destruction, modification or disclosure. Digital information is defined as the representation of facts, concepts, or instructions in a formalized manner suitable for
26 Cyber Security Statistics, Facts & Trends in 2022 26 Cyber Security Statistics, Facts & Trends. Cybercrime comes in many different shapes and sizes, and so do its consequences. What follows is a collection of some noteworthy statistics on the ...
10 Cybersecurity Best Practices that Every ... - Norton Antivirus and anti-malware protections are frequently revised to target and respond to new cyberthreats. If your company sends out instructions for security updates, install them right away. This also applies to personal devices you use at work. Installing updates promptly helps defend against the latest cyberthreats.
The Full Suite of Information Security Policies to ... With over 3-decades of working in Cyber Risk Management & Data Protection. I am a Cyber, Data, and Information security specialist. Here to help you address your cyber, data & information compliance issues and needs. Projects of this type always start with a scoping meeting - Project Meetings are always FREE During the scoping meeting and based on the standard you are working to achieve we ...
How Cybersecurity Policies and Procedures Protect Against ... The policy may then include sections for various areas of cybersecurity, such as requirements for antivirus software or the use of cloud applications. The SANS Institute provides examples of many types of cybersecurity policies.
› what-is-cyber-securityWhat is Cyber Security? | Definition, Types, and User Protection Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It's also known as information technology security or electronic information security. The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common ...
resources.workable.com › cyber-security-policyCompany cyber security policy template - Workable Policy brief & purpose. Our company cyber security policy outlines our guidelines and provisions for preserving the security of our data and technology infrastructure.. The more we rely on technology to collect, store and manage information, the more vulnerable we become to severe security breaches.
Anti-Virus Policy - Information Services - University of ... Policy All computers that are connected to the University of Richmond network must have the standard supported anti-virus... All PC's are to be configured such that they schedule regular updates from the Network Services centralized anti-virus... Macintosh systems are to be configured to schedule ...
getintopc.com › softwares › antivirusAntivirus - Get Into PC in Anti Spyware, Antivirus, Security Acronis Cyber Protect Home Office Free Download. It is full offline installer standalone setup of Acronis Cyber Protect Home Office.
Cyber Security - Policy - Policies and Procedures Library ... A cyber security incident is an event involving an actual or potential malicious actor that threatens the confidentiality, integrity or availability of UQ information assets (electronic or paper) or otherwise contravenes the University's Cyber Security Policy. The source of a cyber security incident may be accidental, malicious or significant ...
› cyber-security-policyCyber Security Policy - GeeksforGeeks Aug 18, 2021 · Cyber Security Policy Last Updated : 18 Aug, 2021 Cyberspace is a complex environment consisting of interactions between people, software, and services, supported by the worldwide distribution of information and communication technology (ICT) devices and networks.
Cybersecurity - NIST Some NIST cybersecurity assignments are defined by federal statutes, executive orders and policies. For example, the Office of Management and Budget (OMB) mandates that all federal agencies implement NIST's cybersecurity standards and guidance for non-national security systems.
PDF CYBER SECURITY Handbook - New Jersey Division of Consumer ... Keep antivirus software up to date. Install software patches and security updates for your antivirus software on a regular basis. They will help protect your computer against new threats as they are discovered. Many vendors and operating systems offer automatic updates. If this option is available, you should enable it.
Antivirus and Malware Policy - CDE Antivirus and Malware Policy. Overview. The number of computer security incidents related to malware and viruses and the resulting cost of business disruption and service restoration continue to escalate. Implementing antimalware and antivirus systems, blocking unnecessary access to networks and computers, improving user security awareness, and early detection and mitigation of security incidents are best practice actions that must be taken to reduce risks and manage the [LEP] computing ...
Cyber security policy template | TalentLyft We recommend employees to follow these best practices: Keep all electronic devices' password secured and protected Logging into company's accounts should be done only through safe networks Install security updates on a regular basis Upgrade antivirus software on a regular basis Don't ever leave your ...
84% of Indian Organizations Falling Short on Data ... According to Veeam's Data Protection Trends Report, 84% of Indian organizations suffered ransomware attacks, making cyber-attacks one of the single biggest causes of downtime for the second ...
Information Security Policy Examples | EDUCAUSE IT Policies at University of Iowa. University of California at Los Angeles (UCLA) Electronic Information Security Policy. University of Notre Dame Information Security Policy. University of Iowa Information Security Framework. Carnegie Mellon Information Security Policy. Stanford University Computer and Network Usage Policy.






























0 Response to "42 antivirus policy in cyber security"
Post a Comment