42 with contemporary antivirus protection it is now possible
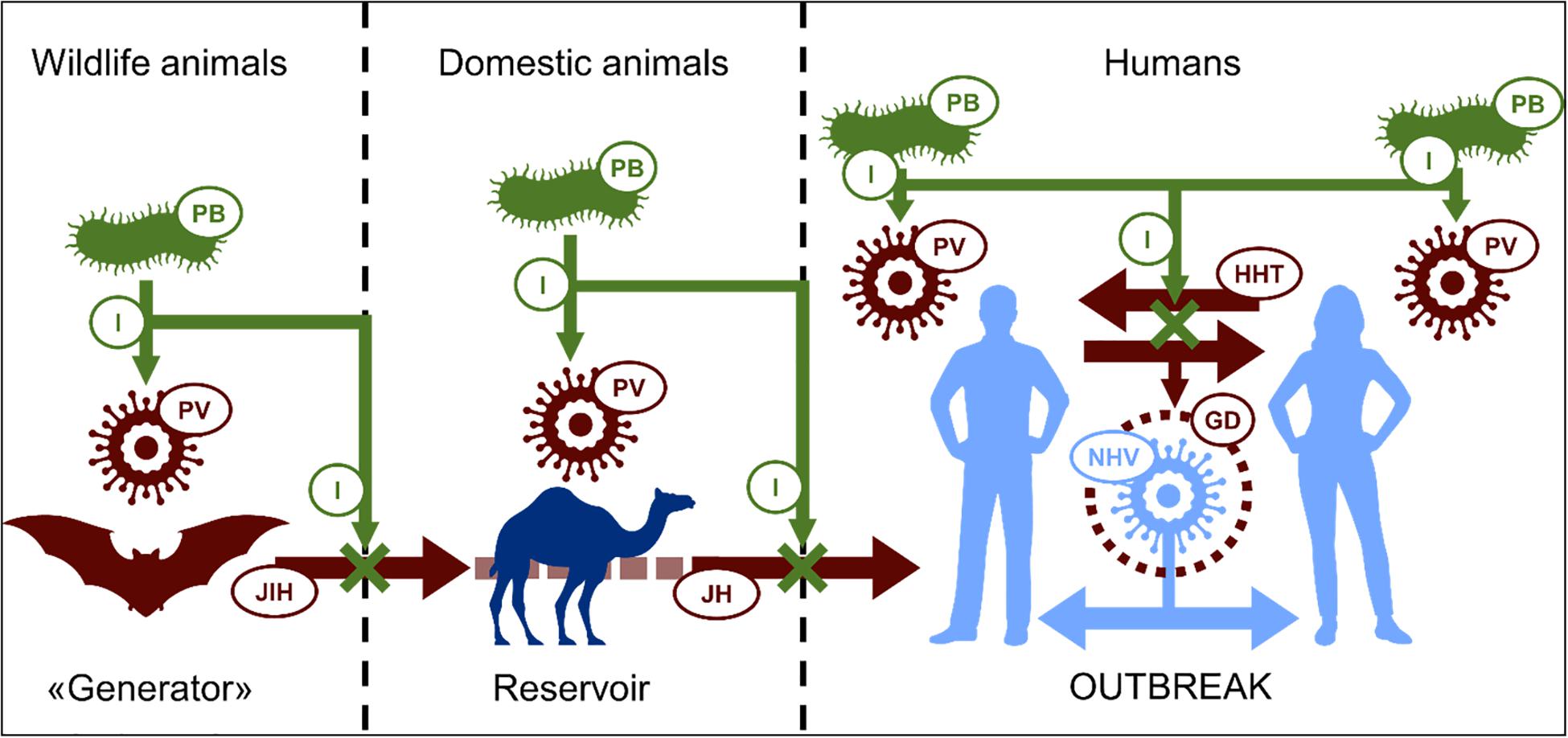
Role of technology in COVID-19 pandemic A way to do early detection of virus spread was proposed in 2009 by Jeremy Ginsberg and their colleagues. According to their work, early spread detection is possible by monitoring health-seeking behavior in the form of online search engine queries. These queries can reach huge number by millions of users around the world each day. What is the future of UK leadership in global health ... The UK is a global health leader. Since the concept of 'health security' first came into parlance with the reconceptualisation of HIV/AIDS as a security threat, 1 the UK has been a leader on global health security. This position was solidified by the broader movement towards the securitisation of non‐traditional security threats post 9/11 (and indeed the anthrax attacks). 2
Discovering Computers - Security Part 2 Flashcards | Quizlet True or False: With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer

With contemporary antivirus protection it is now possible
ESET named a Major Player in two Modern Endpoint Security ... 10.11.2021. Bratislava - ESET, a global leader in cybersecurity, has been recognised as a Major Player in two IDC MarketScape reports - the Worldwide Modern Endpoint Security Enterprise 2021 Vendor Assessment (Doc #US48306021, November 2021), and the Worldwide Modern Endpoint Security SMB 2021 Vendor Assessment (Doc #US48304721, November 2021). COSC 1301 quiz ch.1 Flashcards | Quizlet With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer false looking for a keyboard to project from a device to a flat surface, which would you use virtual keyboard user that requires capabilities of a powerful computer power Top 10 Threats to Information Security | Georgetown University Modern technology and society's constant connection to the Internet allows more creativity in business than ever before - including the black market. Cybercriminals are carefully discovering new ways to tap the most sensitive networks in the world. Protecting business data is a growing challenge but awareness is the first step. Here are the top 10 threats to information security today:
With contemporary antivirus protection it is now possible. 4 Principles of Modern Endpoint Protection (You Must Employ) Only modern endpoint protection can secure your perimeter as firmly as possible, and evolve quickly enough to keep up with hackers' machinations. Furthermore, most modern endpoint protection platforms feature endpoint detection and response (EDR). EDR represents the detection complement to prevention that can help you ensure a far stronger IT ... conveys meaning and is useful to one or more people 2pts ... 8 ) With contemporary antivirus protection , it is now possible to ensure a virus or malware never will attack your computer . ( 2pts ) ( 2pts ) 9 ) The major differences between server computers like the one in the accompanying figure and client computers are that the client typically has more power , more storage space , and expanded ... Why the CIA Triad Is the New Standard For Information Security How ironic that not even companies that specialize in security are impervious to security breaches. Anti-virus software maker BitDefender found this out firsthand when a set of customer usernames and passwords was exposed in plain text. The breach exemplifies how easily IT services can be compromised. 7 Best Free Antivirus Protection You Can Use Right Now
Car Computer Virus? Modern Hackers Could Control Your Car According to Aryeh Goretsky, a researcher at a technology security company called ESET, you shouldn't be too worried. Goretsky states that creating a virus for a car computer is expensive because vehicle manufacturers have proprietary hardware and software. So, attackers could only target one specific make and model at a time. A Dependable Cryptocurrency Wallet Keeps Your Digital ... It will also be possible to find your digital purse if it should be stolen or lost. Use the Internet Cautiously. Do not access your digital wallet in a public space, that is, a public Internet connection. Always use a safe and secure, private Internet connection. Go for additional protection by installing dependable anti-virus software on your ... Imperativeness of cybersecurity in the contemporary world Imperativeness of cybersecurity in the contemporary world. As of now, we are living in a complete modernized digital era where acknowledging with the private data is a more vulnerable one in a typical concern manner. Day by day the ID theft & data breaches are increased globally. On the other side of the flip, the organizations are continually ... Defending Against Modern Malware Attacks in Ruby | by ... Defending Against Modern Malware Attacks in Ruby. Photo by Parker Coffman on Unsplash. Malware attacks are constantly growing. Over 4,000 attacks happen daily in the United States alone. The total damage done by ransomware alone was $20 billion, and the number is constantly growing. It is estimated that a ransomware attack happens every 11 seconds.
What is Antivirus Software? Download Free Antivirus ... - ESET That was mostly in the 1990s and in the beginning of the 2000s. However, with the dramatic growth in numbers of malware in other categories, antivirus programs have evolved into complex security solutions. To ensure their users' security, most contemporary protective products use multiple technologies. There is No Such Thing as True Privacy in the Digital Age Google, which was sued for its practice of scanning Gmail users' emails for advertising purposes, agreed to modify its own use of data following a lawsuit in 2010. "Data has become such a part ... Bus 230 Chapt 1 T/F Flashcards - Quizlet With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer. False You should delete or quarantine flagged attachments immediately. True Never start a computer with removable media inserted in the computer unless you are certain the media are uninfected. False Advances in Antiviral vaccine development Introduction. We are in a transitional time for antiviral vaccines. There are currently licensed vaccines that protect against 15 viral diseases (Table 1), but none have been licensed since the human papilloma virus (HPV) virus-like particle (VLP) in 2006.For the remaining emerging and re-emerging viruses for which vaccine development is a high public health priority, it may be necessary to ...
(PDF) Computer Security and Mobile Security Challenges Computer security, also known as cybersecurity or IT security, is the protection of information. systems from theft or damage to the hardware, the software, and to the information on them, as well ...
CrowdStrike Guide to Frictionless Zero Trust for Modern ... Observations from the front lines of Incident Response & Proactive Cybersecurity Services in 2019 - and key insights for 2020. Read Report. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from ...
The contemporary antivirus industry and its problems - Securelist Nov 21, 2005 · This proactive protection would make it possible to detect a virus and delete it prior to the virus actually being created and appearing on the Internet – and this could be applied to all emerging virus threats. Unfortunately, this simply isn’t possible.
How to Test Antivirus (Is it Really Working and Protecting ... If you have active protection working properly, the simple act of saving the file should trigger an alert. In case the EICAR file is not detected, something is either wrong with your antivirus program, or you are using a rogue or fake security solution. Almost all antivirus applications are able to detect this file and mark it as a threat.
Exam 1 BCIS Flashcards - Quizlet Most e-book readers are usually smaller than smartphones. True With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer. Mobile Which of the following category of users works on a computer while away from a main office, home office, or school? Facebook
How do I know if I already have antivirus software ... Feb 21, 2014 · The status of your antivirus software is typically displayed in Windows Security Center. Open Security Center by clicking the Start button , clicking Control Panel, clicking Security, and then clicking Security Center. Click Malware protection. If Windows can detect your antivirus software, it will be listed under Virus protection.
COVID-19 pandemic: Emerging perspectives and future trends The COVID-19 could become endemic like HIV. It is here to stay, and it is impossible to predict that when this pandemic is supposed to control. This would take a massive effort even if a vaccine was found. It is still possible to control the virus, with effort. Strong and robust control of the virus is required in order to lower the assessment ...
Global security challenges and strategy - Brookings Global security challenges and strategy. Thomas Wright testified before the Senate Committee on Armed Services during its hearing on "Global Security Challenges and Strategy.". A video ...
The evolution of industrial cybersecurity and contemporary ... In addition to anti-spam and conventional anti-virus measures, intrusion detection, log collection and traffic analysis tools were also introduced to enable real-time network monitoring. With the introduction of IT asset management tools, it is now possible to monitor and manage the devices connected to the network, including the access and ...
PDF MODERN PROTECTION AGAINST ATTACkS FROM THE INTERNET gurations should be possible in a centralized manner via the system. Higher security standards were called for in the e-mail system in Kiel too. The aim: to ensure greater protection against spam and malware such as viruses and Trojans. THE SOLUTION Thanks to a next generation firewall, the security system at the FH Kiel is now up to date.
Best Antivirus Software for 2022 - CNET
Covid-19 and the Apocalypse: Religious and Secular ... The current Covid-19 pandemic has led to existential crises. One way of finding meaning in this is through apocalyptic narratives. We differentiate between religious (based upon eschatology) and secular apocalypticism (based upon radical political and economic change) and argue that both are to be found in the wake of Covid-19 infection.
What is Information Security & Why is it Important? To make this possible, systems need to be updated and software backed up. "The careful implementation of information security controls is vital to protecting an organization's information assets as well as its reputation, legal position, personnel, and other tangible assets," the NIST said.
(PDF) Issues regarding cybersecurity in modern world ... Issues regarding cybersecurity in modern world H. Geldiyev, M. Churiyev, R. Mahmudov 1 Introduction Information security has always been a priority for any of the areas of human activity. Particularly acute is the issue of information security in our time - in the period of informatics and computerization. A new type of information security ...
Top 10 Threats to Information Security | Georgetown University Modern technology and society's constant connection to the Internet allows more creativity in business than ever before - including the black market. Cybercriminals are carefully discovering new ways to tap the most sensitive networks in the world. Protecting business data is a growing challenge but awareness is the first step. Here are the top 10 threats to information security today:
COSC 1301 quiz ch.1 Flashcards | Quizlet With contemporary antivirus protection it is now possible to ensure a virus or malware never will attack your computer false looking for a keyboard to project from a device to a flat surface, which would you use virtual keyboard user that requires capabilities of a powerful computer power
ESET named a Major Player in two Modern Endpoint Security ... 10.11.2021. Bratislava - ESET, a global leader in cybersecurity, has been recognised as a Major Player in two IDC MarketScape reports - the Worldwide Modern Endpoint Security Enterprise 2021 Vendor Assessment (Doc #US48306021, November 2021), and the Worldwide Modern Endpoint Security SMB 2021 Vendor Assessment (Doc #US48304721, November 2021).






























/does-windows-10-need-antivirus-protection-4767578-1-7d4628e2729a47dea0a08e5cb2323cab.png)



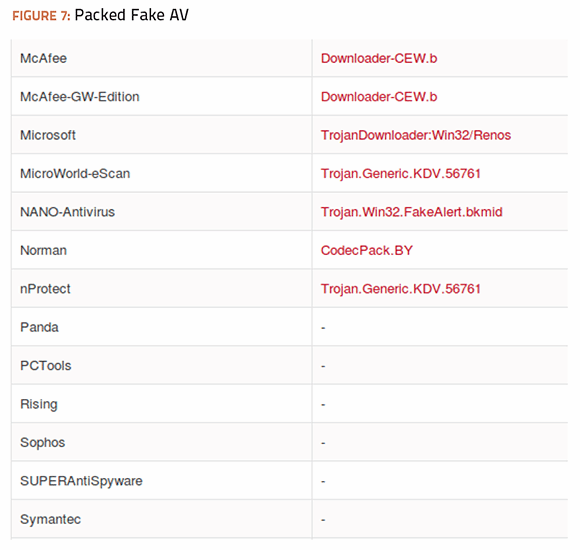
0 Response to "42 with contemporary antivirus protection it is now possible"
Post a Comment