39 which of the following could be detected by antivirus software
INFORMATION SECURITY: Theory and Practice DHIREN R. PATEL · 2008 · ComputersIn the past , we could detect viruses by searching for virus signatures ... These encrypted viruses pose few problems for modern antivirus programs ... Which of the following keyloggers cannot be detected by ... «Which of the following refers to applications or files that are not classified as viruses or Trojan horse programs, but can still negatively affect the performance of the computers on your network and introduce significant security risks to your organization?
Pluralsight download. - veresszilard.de g. Step by step guide from : Batch Download Pluralsight Courses for Offline Viewing on Mac and WindowsPluralsight Free Weekend — 13th to15th August. 1 of 67 antivirus programs detected threats, see the report. pluralsight, Pluralsight. Comment if you have any issues or give a thanks.

Which of the following could be detected by antivirus software
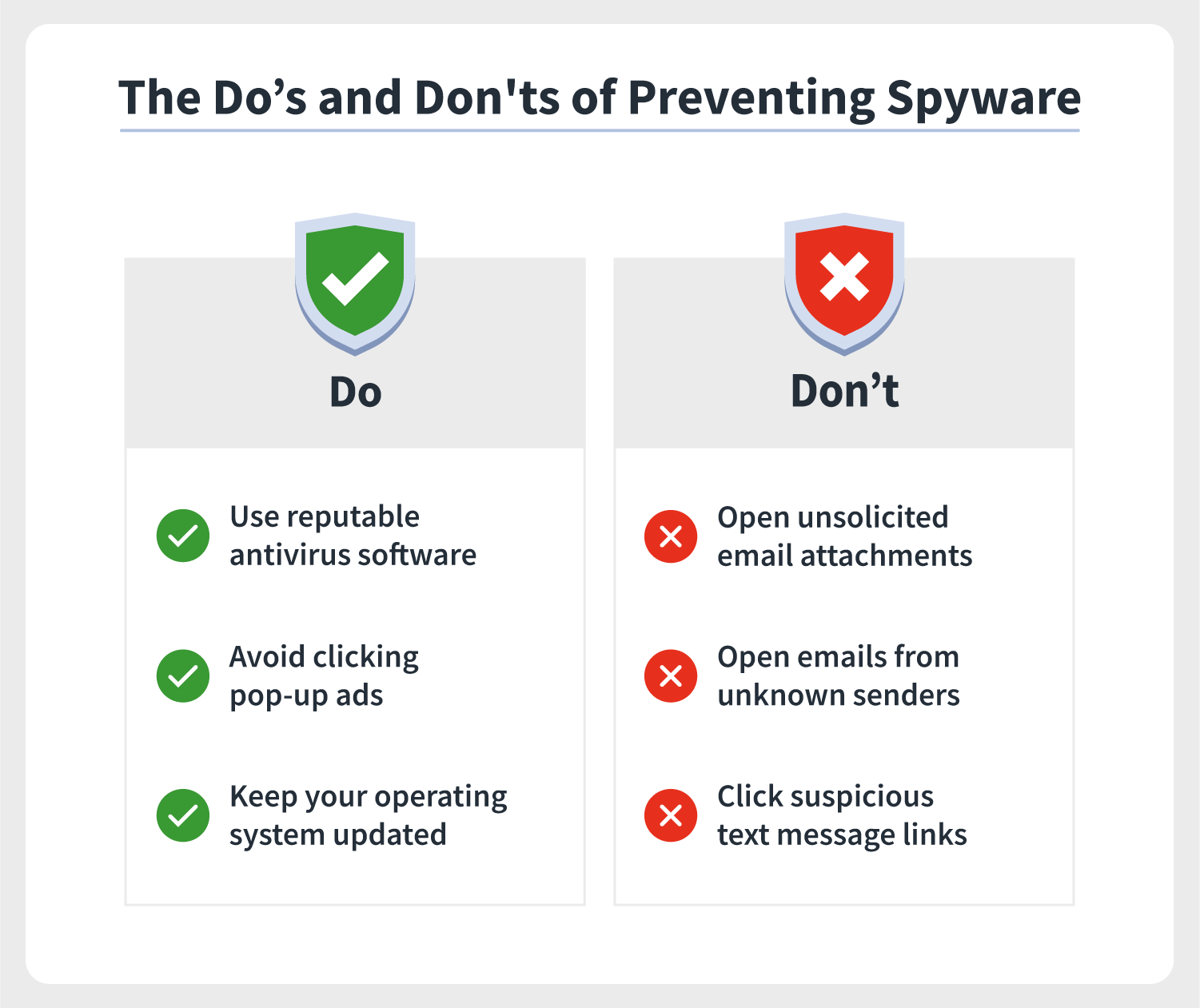
Virus link to send. - kinderleicht-mit-anja.de If you do open it, do not open any attachments or click on any links. 13 thg 1, 2022 If you send or receive money with Apple Pay (U. When you open a spam email that has a virus, the computer gets infected. Aug 03, 2016 · I wanted to find updated anti-virus software. Those who don't know how to use VCRT, VBug or VBug Map. Antivirus Bypass Techniques: Learn practical techniques and ... Nir Yehoshua, Uriel Kosayev · 2021 · ComputersThe rate can be 70%, for example, that the file is detected as malicious and the antivirus software will stop it from running. To take advantage of this ... Q.2657: Which of the following procedures would MOST ef Antivirus software will not necessarily identify illegal software, unless the software contains a virus. Disklessworkstations act as a preventive control and are not effective, since users could still download software from other than diskless workstations. Policies lay out the rules about loading the software, but will not detect the actual ...
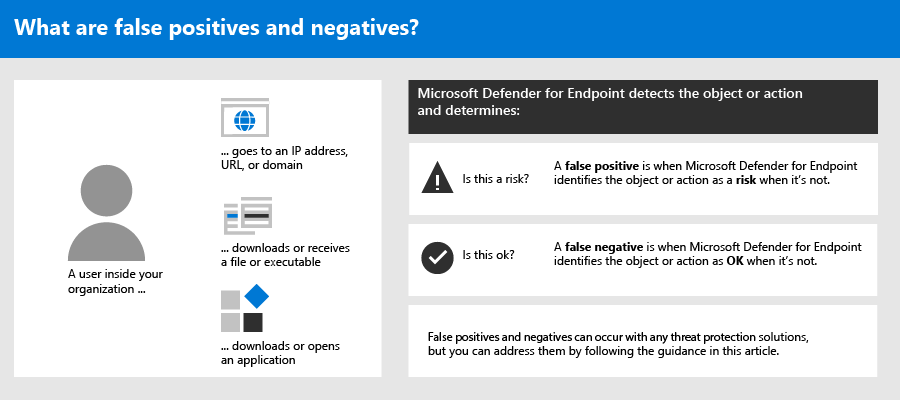
Which of the following could be detected by antivirus software. CHAPTER 7 Flashcards | Quizlet When antivirus software detects malware, which of the following would not be a course of action you could take? a. Conduct a heuristic analysis. b. Repair the infection. c.Put the infected file into quarantine. d. Delete the infected file. Threats detected by Microsoft Defender Antivirus ... What to expect when threats are detected. When threats are detected by Microsoft Defender Antivirus, the following things happen: Users receive notifications in Windows.. Detections are listed in the Windows Security app on the Protection history page.. If you've secured your Windows 10 devices and enrolled them in Intune, and your organization has 800 or fewer devices enrolled, you'll see ... Ispoofer pro free. - panimaria.de Follow Following Unfollow. Fake GPS Android latest 2. 253 votes, 127 comments. 3. you need to get the iSpoofer activation key to enjoy using the software. iSpoofer Activation Key 2022 will allow you to be fake your iPhone, iPad, or iPod GPS location to show you where you need to be. Security+ Questions Flashcards | Chegg.com Which of the following types of file sets can be used to compare the characteristics of known instances of malware that the antivirus software detected? Signature An area of the network infrastructure that allows a technician to place public facing systems into it without compromising the entire infrastructure is which of the following?
Which Of The Following Could Be Detected By Antivirus ... Which Of The Following Are Antivirus Detection Types? The most common methods of detecting viruses are scanning, integrity checks, intercepting, and heuristics. While scanning, interception, and other methods have been on the rise for several years, none is normally as popular as anti-virus software. Which Of The Following Is An Antivirus Software? Avoiding Computer Viruses Flashcards - Quizlet Which of the following could be detected by antivirus software? a) E-mail attachments b) Spam c) Downloaded images d) Macros. d) Macros. Which of the following are considered slightly different from viruses as they can run independently of host file execution? a) Spam b) Worms Nicehash gpu error. - tiertaxi-renner.de Ask questions Radeon RX5700 GPU Temp/Load not detected Mining XMR with Xmrig sometimes will display "read error: end of file" on NiceHash Miner 3. gtx 1080 with 8 gib video ram 32 gib ram core i7-6700 windows 10 pro 64-bit fall creator update geforce driver version 388. 0 software thingy, BUT what you can do is underclock your card. NVIDIA. How Does Antivirus Software Work? | 2022 | U.S. News If you've chosen the right antivirus software, you're unlikely to be faced with a detected but untreated virus. "In Windows, most antivirus software should be able to remove anything it wants to ...
Microsoft Defender Antivirus event IDs and error codes ... Microsoft Defender Antivirus has detected malware or other potentially unwanted software. For more information, see the following: ... Microsoft Defender Antivirus could not load antimalware engine because current platform version is not supported. Microsoft Defender Antivirus will revert back to the last known-good engine and a platform update ... Detect Antivirus on Windows using C# - Stack Overflow In WMI mode, software manufacturers determine their own product status and report that status back to Windows Security Center through a WMI provider. In both modes, Windows Security Center tries to determine whether the following is true: An antivirus program is present. The antivirus signatures are up-to-date. Could not mount disk2s3 com apple diskmanagement disenter ... I was getting the following error: I opened Search: Could Not Mount Disk2s3 Com Apple Diskmanagement Disenter Error2# diskutil mount disk0s2 Volume on disk0s2 failed to mount because it object map error: om: btn: invalid o_oid (0x60b2e) Object map is invalid The volume /dev/rdisk1s1 could not be. Chrome issue. - softwaretraining-pfeifer.de If your problem of the Windows 10 Firewall issue remains even after resetting Google Chrome, you can uninstall the Chrome application and install it again by following these steps. 3. Chrome 88 beta was released on December 3, 2020 and is expected to become the stable version in the third week of January 2021.
Which Of The Following Are Antivirus Detection Types ... What Is Antivirus Detection? It is a type of software that can protect, scan, detect, and delete viruses on a computer. To provide real-time protection against virus attacks, most antivirus software automatically runs on the background once installed.
Q.78105: Which of the following viruses cannot be detec Therefore, polymorphic viruses cannot be detected by. signature-based antivirus. Answer A is incorrect. A macro virus is a virus that consists of a macro code which infects the. system. A Macro virus can infect a system rapidly. Since this virus has VB event handlers, it is. dynamic in nature and displays random activation.
Q.2657: Which of the following procedures would MOST ef Antivirus software will not necessarily identify illegal software, unless the software contains a virus. Disklessworkstations act as a preventive control and are not effective, since users could still download software from other than diskless workstations. Policies lay out the rules about loading the software, but will not detect the actual ...
Antivirus Bypass Techniques: Learn practical techniques and ... Nir Yehoshua, Uriel Kosayev · 2021 · ComputersThe rate can be 70%, for example, that the file is detected as malicious and the antivirus software will stop it from running. To take advantage of this ...
Virus link to send. - kinderleicht-mit-anja.de If you do open it, do not open any attachments or click on any links. 13 thg 1, 2022 If you send or receive money with Apple Pay (U. When you open a spam email that has a virus, the computer gets infected. Aug 03, 2016 · I wanted to find updated anti-virus software. Those who don't know how to use VCRT, VBug or VBug Map.


/Bitdefender-d98d8a9c6c0f495188b40291010a0304.jpg)








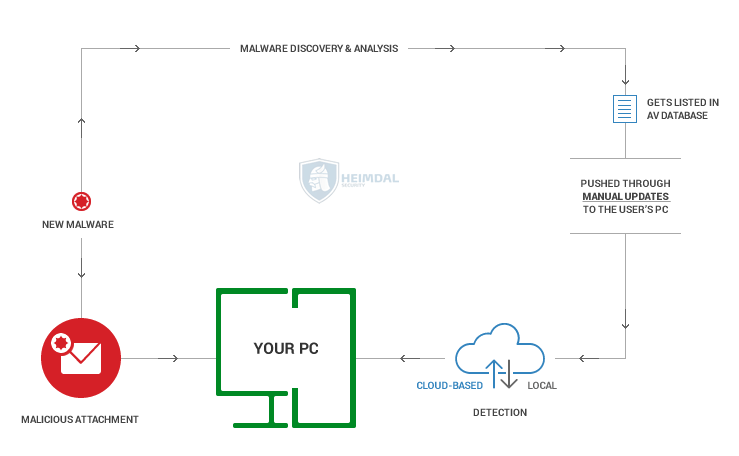







:max_bytes(150000):strip_icc()/Bitdefender-d98d8a9c6c0f495188b40291010a0304.jpg)
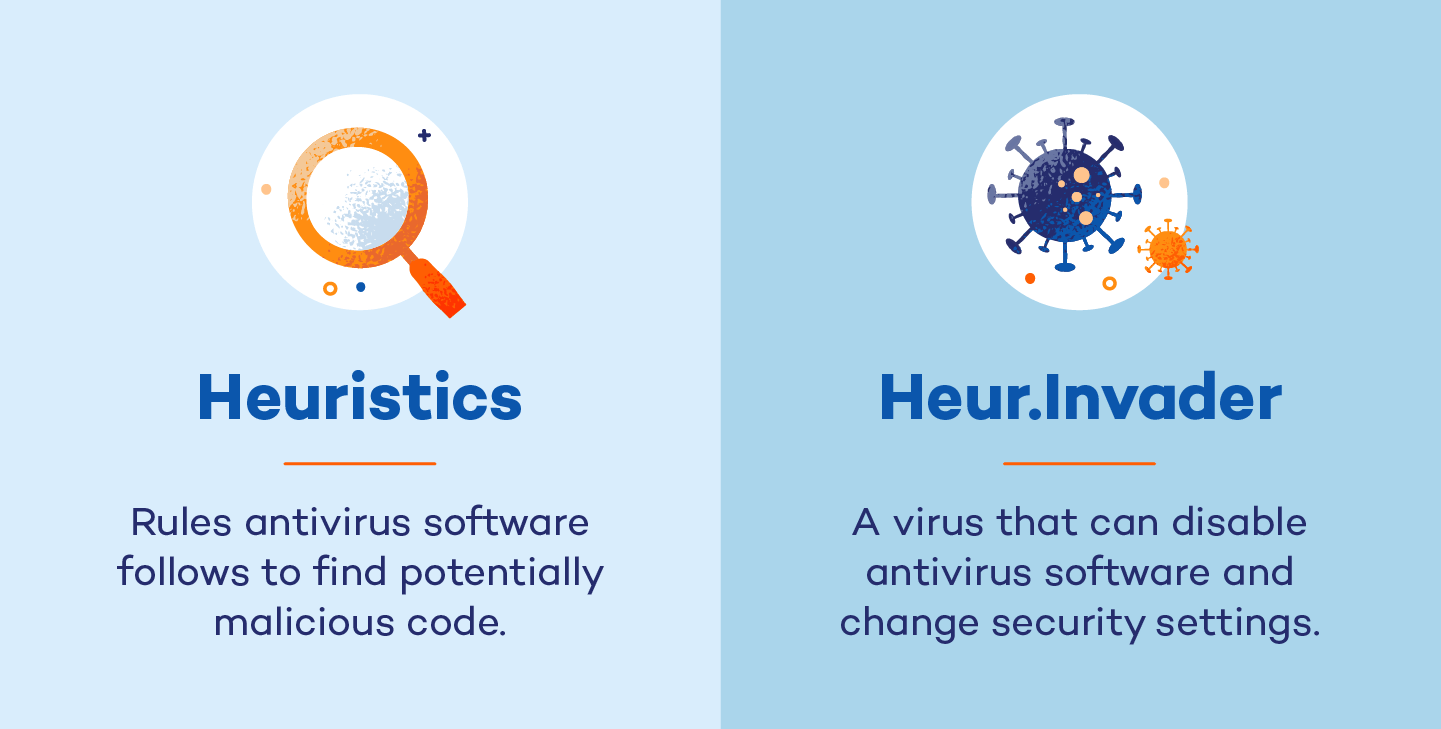











0 Response to "39 which of the following could be detected by antivirus software"
Post a Comment